Wading through the hype to what security threats matter most
By Javvad Malik, Technical Evangelist
It's a sad indictment of our industry that style often trumps substance, and marketing hype is often treated as a substitute for sober contemplation of security threats based on real-world conditions and intelligence.
Indeed, intelligence is what we need the most when we are being bombarded by all manner of information from all sides; all shouting about the latest threats. Vulnerabilities in IoT will not just bring down your company, but entire cities. The payment terminal can be hacked to take all your money. Artificial intelligence is both the future of what you need, and will be the cause of your eventual downfall.
Security teams are dealing with an ever-increasing number of threats. Each year, the information security community identifies roughly 12,000 new threats, each impacting different applications and with their own unique characteristics when it comes to exploitation and remediation.
So, how do we make sense of this? Particularly given how many companies are underfunded or ill-equipped to deal with such a variety of threats.
Fortunately, the information is already available, we just need to turn that information into a bit of intelligence to know where to focus our efforts.
To understand this, I wanted to put data in the driving seat. Companies shouldn't be spending time and effort trying to remediate low-impact, and less likely threats. Rather, they should focus on what is important. Now, not to be controversial, but using something like CVSS, or an internal risk matrix is often not the most practical of methods.
Rather, we need to peel back one layer and ask - what is the actual root cause of these threats? As in, how are these threats making their way into our enterprise.
To do this, I examined 100 threat intelligence reports published between July and August 2019 across a variety of different vendors. These 100 reports offered an insight into the most common avenues of ingress used by threat actors. After all, if we can identify this, we can focus our resources on closing those particular doors - or even just guard them more intently.
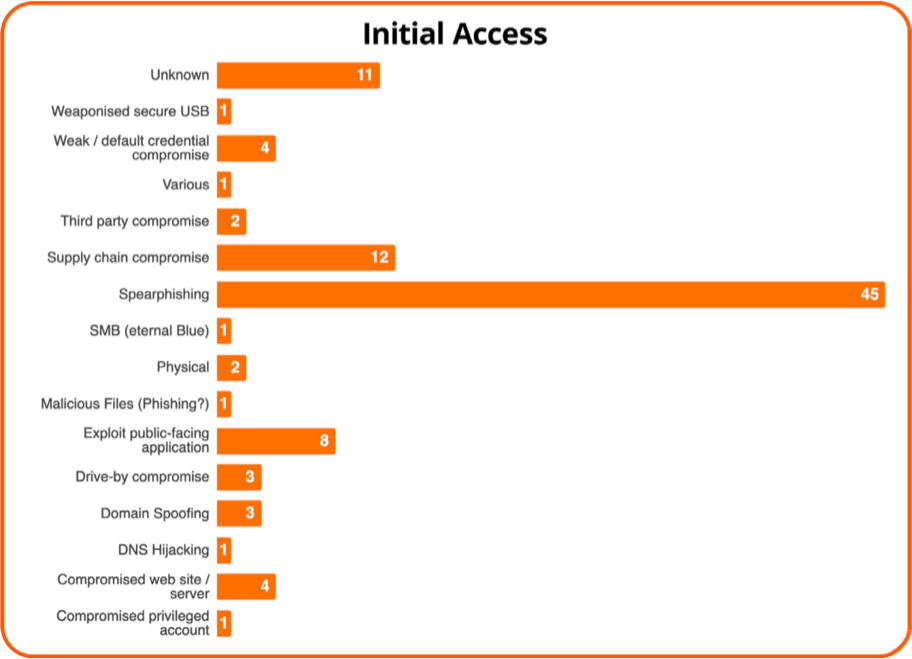
As the table shows, the overwhelming number of threats focus on exploiting the human through either phishing, spearphishing, or other social engineering attacks which in some cases also include supply chain compromise.
Exploitation of public-facing applications, web sites, or servers was also a common method. So, if companies only focussed on raising awareness amongst its staff, and ensuring external-facing systems were patched and secured, they could, in theory prevent the majority of attacks.
The key to remember is that ransomware, or cryptojacking isn't the problem, they're a symptom of a broader concern - namely, how they got in to your organisation in the first place.
Look within your own organisation, take your internal data and arrive at your own conclusions. Maybe credential stuffing is your biggest challenge, so deploying a control like MFA may be the first thing to focus on.
Context, as always, is king.


