Three Things to Know About Ransomware Attacks
By Cheryl Tang, Director Product Marketing
Ransomware attacks continue to make headlines and show no sign of slowing down. Last year alone, the United States suffered 65,000 ransomware attacks. These attacks not only bring organizations to a complete standstill, but also impact surrounding communities — forcing hospitals to turn away patients, shutting down schools for days or weeks, and preventing citizens from accessing critical government services.
Because ransomware attacks are so disruptive, preventing and preparing for ransomware attacks is not only a business priority, but also a national security issue. Senior company leaders, including the Board of Directors, CEOs, and CISOs, are asking if their organization is vulnerable to ransomware attacks. To help security professionals answer that question, here are three things to know about ransomware attacks.
Ransomware attacks are multi-stage, human-operated and increasingly leverage cybercriminal organizations to gain initial access. Ransomware was once sent directly to users as the "first stage" payload, usually as an email attachment. However, Proofpoint Threat Research observed that ransomware as a first stage payload peaked in 2017 with the Locky ransomware outbreak. While first stage ransomware does still occur, the majority of ransomware attacks today involve initial access brokers who use first stage malware like The Trick, Dridex or Buer Loader to compromise an organization and then sell that initial access to ransomware operators to exfiltrate and encrypt data.
Ransomware actors are big game hunting. Instead of "spray and pray" ransomware campaigns, ransomware actors are focusing less on volume and more on targeting specific organizations and industries. According to the latest FBI IC3 report, recent ransomware attacks "have been more targeted and sophisticated, and costly" than past opportunistic attacks. Another growing tactic to increase their monetization efforts is data exfiltration extortion. A vast majority of ransomware attacks now include the theft of corporate data and the threat of releasing that data to the public if the ransom isn't paid quickly.
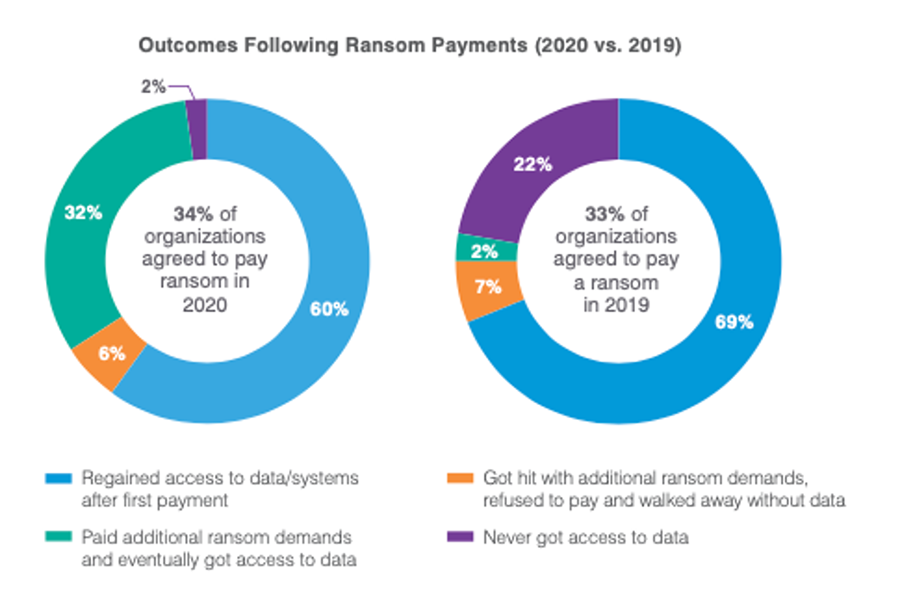
In the latest State of the Phish report, we find that 34% of organizations surveyed were infected and opted to pay the ransom in 2020. While these victims hoped to regain access to data and systems, fewer got what they were promised. Nearly a third ended up paying an additional ransom.
Ransomware actors use a variety of infection vectors. While email is certainly a common attack vector, recent high-profile attacks have resulted from other attack vectors like stolen VPN credentials. Other common ransomware attack vectors include Remote Desktop Protocol (RDP) and VPN vulnerabilities and misconfigurations. Preventing ransomware requires addressing these three common infection vectors.
To learn more about ransomware, including how you can better protect your company, watch our webinar "Ransomware Attacks on the Rise — What You Need to Know."