Summiting the Pyramid of Pain by sharing TTP detections in real time
By Peter Rydzynski, IronNet Threat Analysis Lead, and Morgan Demboski, IronNet Threat Intelligence Analyst
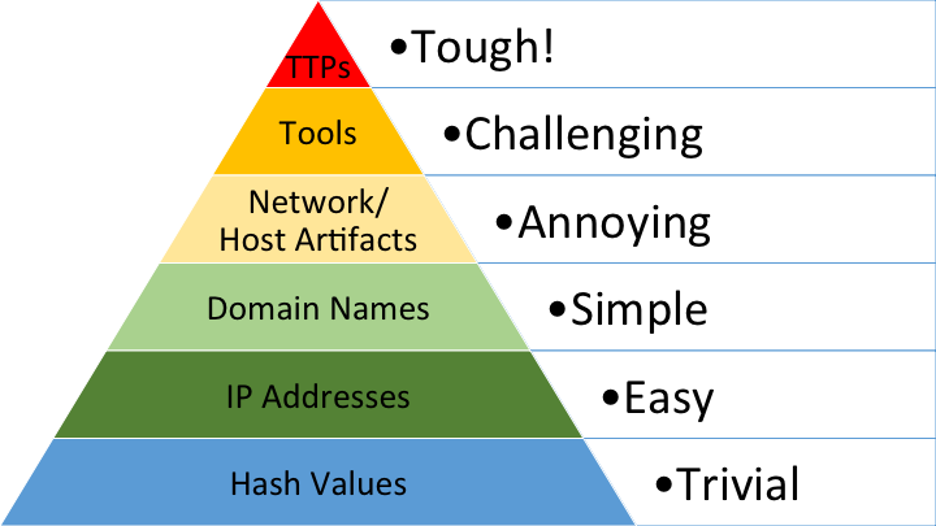
David J. Bianco's "Pyramid of Pain" Threat Hunting Framework is nothing new. Consisting of six logical groupings of indicators of compromise (IOCs), the pyramid illustrates that not all IOCs are created equal, while also specifying the relative level of difficulty for a malicious attacker to avoid detection. In short, it maps how hard it would be for a threat actor to move away from a particular IOC or attack feature that defenders could use to detect them.
It is broadly accepted in the analyst community that a cyber attacker can easily change hash values, IPs, and domains — the three lowest levels. On the other hand, it is also widely known that TTPs (tactics, techniques, and procedures) — the top-level — are the most difficult for an attacker to change. Therefore, TTPs, which really boil down to adversarial "behaviors," are the best type of indicators for defenders to focus on when attempting future detections based on previous knowledge.
Knowing this, enterprises will want to direct cybersecurity priorities and investments toward the apex of the pyramid. With an eye on TTPs, network detection and response (NDR) tools yield more robust detections that are tolerant of changes in an adversary's IOCs, forcing attackers to overhaul their existing tooling in order to remain undetected. Given how daunting this task is for adversaries, cyber defenders gain an upper hand by detecting campaigns before they advance along the kill chain and across companies or sectors.
The state of IOC sharing has matured significantly, with many free and paid sources of threat intelligence offering hash, IP, and domain-based IOC feeds. There have also been great improvements to open-source protocols for sharing intelligence, such as STIX/TAXII, which now can contextualize indicators directly in the protocol. There are even platforms that enable the cybersecurity community to share directly with each other, like AlienVault OTX. Finally, there are some research tools like Yara that have moved the community higher up in the pyramid by enabling the detection of adversarial tools and malware instead of hash values.
These are all positive leaps forward for information sharing and should not be overlooked, but these advancements are entirely isolated to traditional IOCs that are relatively trivial for an attacker to avoid. As such, analysts cannot rely solely on these traditional IOCs to detect malicious activity. What had been missing for years is a mechanism that enables the community-wide sharing of TTPs in real time.
A platinum sponsor of BlackHat and part of this year's hand-selected Black Hat NOC, IronNet is filling that technology gap. Beyond the fact that IronNet focuses on detecting malicious activity through TTPs (using fine-tuned behavioral analytics that cut down on false positives), we also have the unique capability of sharing these TTPs across our threat-sharing Collective Defense platform IronDome. Few organizations even have behavioral detection capabilities, but none can correlate behaviors across communities of companies, supply chains, sectors, and/or government organizations.
This Collective Defense approach empowers threat hunters to summit the Pyramid of Pain to get ahead of the adversaries.