Re: Black Hat USA mass reg email
July 22, 2012 11:40am PDT
"Hanlon's Razor states, "Never attribute to malice that which is adequately explained by stupidity"
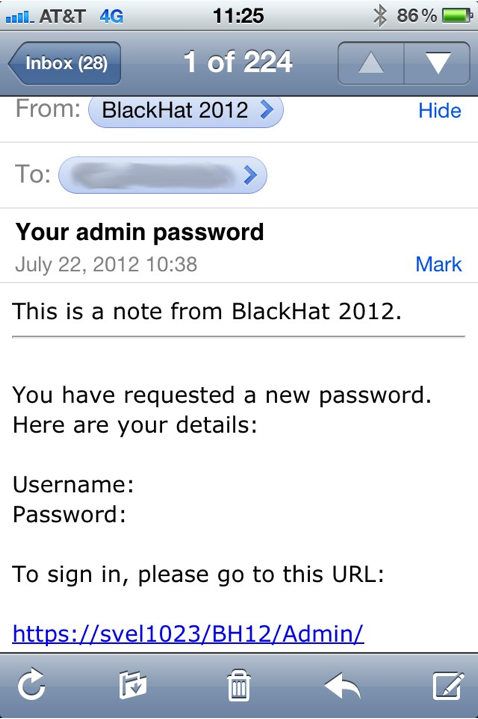
Greetings, from one of the most hostile, and accountable networks on earth! Today approximately 7,500 of you received an email 'from' Black Hat 2012, (email address: itn-international.com)
(picture via @m1a1vet)
We love to tease people that your systems need to be ready to hold their own if joining the Black Hat network. In this frame of mind, the community very correctly expected a prank or act of malice.
The far more concerning thought would be how is ANYONE other than Black Hat emailing the registered delegates for the 2012 show? Some data is shared on a need-to-know basis with some key partners, one of which is ITN who is handling our on-site registration and check-in systems at the show this year.
For those of you intimately acquainted with Black Hat, our show is powered by an army of volunteers- they handle everything from building classrooms for training, proctoring speakers and sessions, to checking you in at registration.
This morning, some idle hands browsed their way to a screen that looked like this:
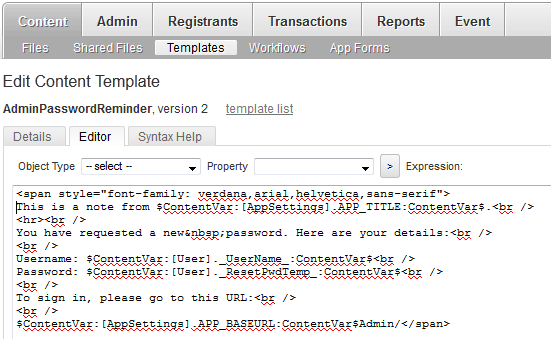
We would provide a better screenshot, but that actually ends in sending an email. Call it a 'feature'. The link provided in the email is to an onsite host on our registration network.
We have reviewed the server logs, we know the user, host, and have spoken with the volunteer who has emailed each of you this morning.
Executive Summary:
Our most valued assets at Black Hat are our delegates and their privacy. We work very hard to maintain that. We want everyone to come to Black Hat to learn and enjoy their time without fear of having their personal or professional information compromised. We are happy to report there are no signs of compromise.
The email this morning was an abuse of functionality by a volunteer who has been spoken to. This feature has since been removed as a precautionary measure.
…does this mean we should submit a VERIS report?
Trey Ford
General Manager, Black Hat


